Cyber Security: Zero Trust Strategy & Solutions
One NFF Team – Unparalleled 24x7x365 Security
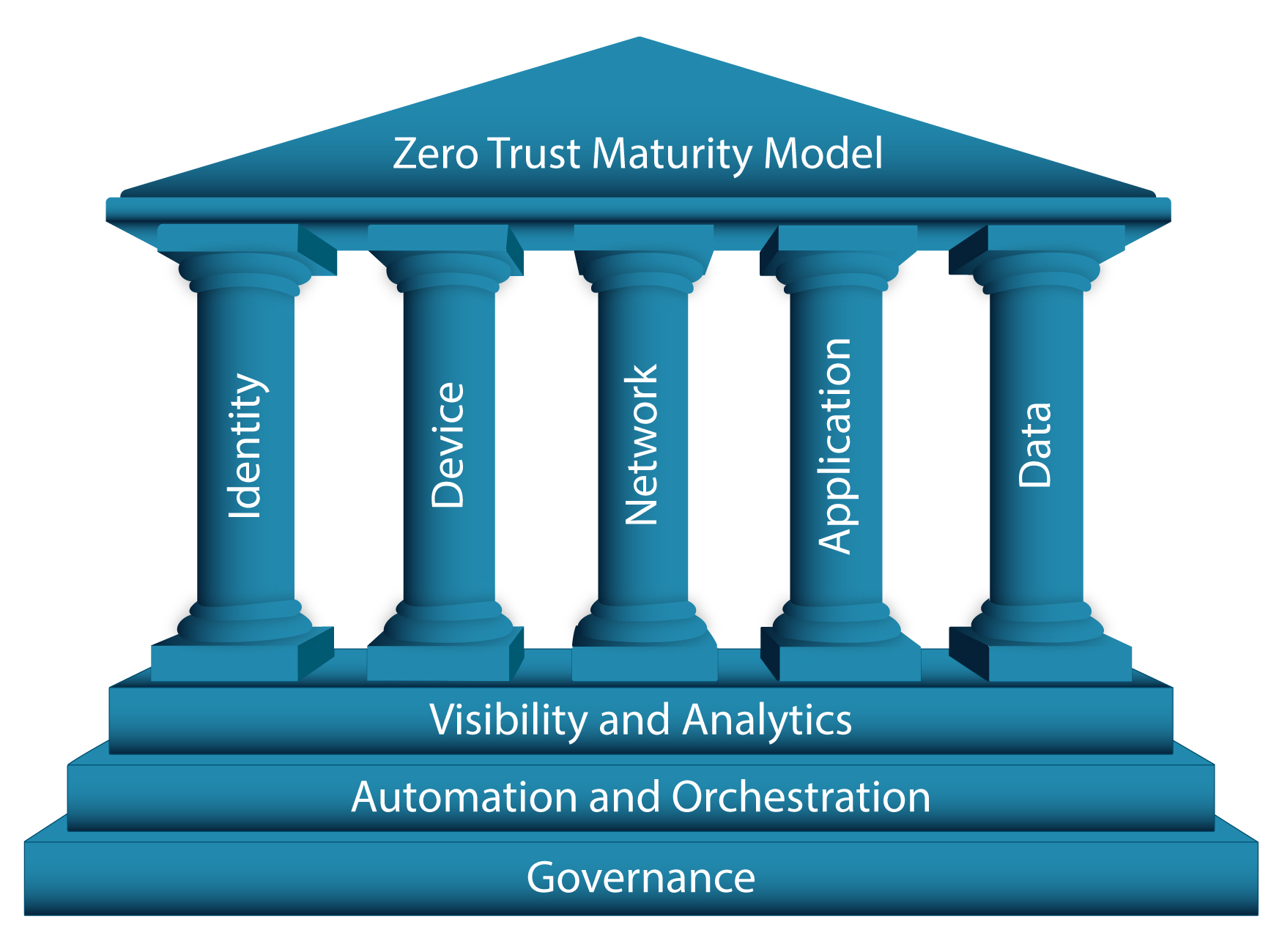
In today’s rapidly evolving threat landscape, traditional perimeter-based security is no longer enough. A Zero Trust Strategy ensures that every user, device, and application is continuously verified before gaining access to critical resources—minimizing the risk of breaches, insider threats and ransomware impact.
Navigating the complexities of Zero Trust can be overwhelming, that’s where our expertise comes in. With NFF’s deep architecture and cybersecurity expertise combined with industry leading Zero Trust solution partners, we provide tailored solutions that align with your organization’s unique security needs. From identity and access management (IAM) to network segmentation and endpoint security, we help you implement a robust Zero Trust architecture with industry leading technologies and solutions.
Let NFF build a resilient, future-proof security framework that ensures trust is never assumed and threats are contained.
Identity & Access
Network &
Endpoint &
Managed Risk &
Threat Detection &

Effective Identity and Access Management (IAM) is the foundation of a Zero Trust security model. Our solutions provide seamless authentication, adaptive access controls, and granular policy enforcement to ensure only authorized users can access critical systems and data. By integrating multi-factor authentication (MFA), single sign-on (SSO), and role-based access control (RBAC), we create a security-first approach that minimizes unauthorized access and insider threats.
With advanced identity governance and continuous monitoring, we ensure that our clients gain visibility and control over user activity while enhancing compliance and operational efficiency.

Modern businesses require network and application security solutions that safeguard against evolving cyber threats while ensuring uninterrupted performance. Our approach secures network traffic with micro-segmentation, next-generation firewalls, and real-time threat prevention mechanisms.
By embedding security within applications and cloud environments, we minimize vulnerabilities and prevent lateral movement of malicious actors. With AI-driven threat intelligence and automated response capabilities, organizations benefit from a resilient security framework that adapts to dynamic IT landscapes and evolving attack vectors.
Every device connected to your network represents a potential attack surface, making endpoint and device security a critical component of Zero Trust. Our solutions enforce strict access policies, leverage endpoint detection and response (EDR) tools, and apply real-time behavioral analytics to identify and mitigate risks.
By securing endpoints—including desktops, mobile devices, and IoT assets—with proactive threat prevention and automated remediation, we reduce exposure to cyber threats while maintaining seamless user experiences.
Regulatory compliance is more complex than ever, with constantly changing standards, expanded enforcement, and increased penalties. Businesses must navigate overlapping frameworks, industry-specific regulations, and evolving cybersecurity mandates, making compliance a resource-intensive challenge with significant financial implications.
Without a structured approach, organizations face inefficiencies, audit stress, and regulatory compliance gaps. NFF’s compliance readiness service simplifies adherence to the myriad of requirements by transforming it into a structured, repeatable process that eliminates redundant efforts. Using a common control framework, shared libraries for control response, evidence, and risk management documentation, we reduce the burden of audits while ensuring continuous alignment with multiple standards.
Our approach streamlines policy implementation and minimizes the effort required to maintain up-to-date compliance records. By reducing unnecessary work and improving overall efficiency, we help businesses enhance security, mitigate risk, and focus on their core objectives with confidence.
Rapid threat detection and response are crucial in mitigating cyber risks before they escalate into significant security incidents. Our advanced security operations solutions integrate AI-driven analytics, security information and event management (SIEM), and extended detection and response (XDR) capabilities to proactively identify, investigate, and contain threats.
With automated incident response, continuous monitoring, and forensic analysis, organizations can minimize downtime and protect their critical assets. By leveraging real-time intelligence and adaptive security measures, we help businesses stay ahead of emerging threats and maintain a strong security posture.